Understanding the Distinction: Malware Vs. Spyware Explained by MalwareFox

Understanding the Distinction: Malware Vs. Spyware Explained by MalwareFox
When it comes to computer security, there are a lot of terms that can be confusing. Two of the most common terms are malware and spyware. Many people use these words interchangeably, but they actually have different meanings. Both malware and spyware can be extremely harmful to your computer, so it’s important to know how to protect yourself from them.

Stay malware-free with reliable antivirus
Don’t compromise your Data and Privacy. TotalAV is a top-notch antivirus program that handles various viruses, trojans, and other malware that may target your devices. It will safeguard your devices and enhance your system performance.
4.9/5
⭐ Editor’s Choice
✔️ Excellent Malware Detection
✔️ Multiple set of Features
✔️ 30 Day Money-Back
In this blog post, we will discuss the difference between malware and spyware and how to protect your computer from both.
Disclaimer: This post includes affiliate links
If you click on a link and make a purchase, I may receive a commission at no extra cost to you.
What is Malware?
Malware is a catch-all term for any type of malicious software that can infect your computer, including Spyware. However, not all malware is created equal. There are many different types of malware, each with its own purpose and method of infecting computers. Some common types of malware include viruses, spyware, adware, Trojan horses, and ransomware.
Other than that, malware can also be used to collect sensitive information, such as passwords and credit card numbers. This type of malware is often used by criminals to commit identity theft or financial fraud. In some cases, malware can even be used to gain access to confidential information, such as government secrets or trade secrets.
How Malware Works?
As we know, there are many different types of malware, including viruses, Trojans, worms, adware, and ransomware. These can be spread in a variety of ways, including email attachments, downloads from malicious websites, and drive-by downloads.
Once malware is on your computer, it can do a lot of damage. It can delete files, steal personal information, corrupt data, and even disable your computer altogether. In some cases, malware can allow hackers to gain remote access to your computer and use it to launch attacks against other computers. If you think your computer may be infected with malware, it’s important to run a scan with an anti-malware program as soon as possible.
What is Spyware?
Spyware is a type of malware that is designed to collect information about you without your knowledge or consent. It can track your online activity, steal sensitive information like passwords and credit card numbers, and even record your conversations.
Spyware can be installed on your computer in a variety of ways, including email attachments, downloads from malicious websites, and drive-by downloads. Once it’s on your computer, it can be difficult to remove. In some cases, spyware can even disable your anti-virus software and other security tools.
How Spyware Works?
As we know, Spyware can track which websites you visit, and what you type into web forms, and even collect sensitive information like credit card numbers and login credentials. Spyware usually infection computers through downloads from malicious websites or email attachments. Once installed on your computer, it will start collecting data and sending it back to the hacker who installed it.
Malware vs. Spyware Comparison Table
| Sr No. | Difference Parameters | Malware | Spyware |
|---|---|---|---|
| 1. | Definition | Malware is a catch-all term for any type of malicious software that can infect your computer | Spyware is a type of malware that is specifically designed to gather information about you without your knowledge or consent |
| 2. | Danger | Malware like Ransomware is more dangerous than Spyware | Spyware is less dangerous than some malware |
| 3. | Damage | Malware can delete files, steal personal information, corrupt data, and even disable your computer altogether | Spyware can track your online activity, steal sensitive information like passwords and credit card numbers, and record your conversations |
| 4. | Types | Viruses, Trojan, Ransomware are the types of malware | Keyloggers and browser hijackers are the types of spyware |
| 5. | Replication | Malware such as viruses can replicate themselves | Spyware cannot replicate itself |
| 6. | Detection and Removal | Malware can be detected and removed using antimalware solutions | Spyware required specially designed software called AntiSpyware to get detected |
How to Protect Your Computer from Malware and Spyware?
Update Your Antivirus Software
One of the most important things you can do is to keep your antivirus software up-to-date. Cybercriminals are constantly developing new ways to avoid detection. By keeping your antivirus software up-to-date, you will make sure that it can detect and remove the latest threats.
Use a Reputable Antivirus Software
It’s important to use reputable antivirus software. Some antivirus programs are better at detecting and removing malware than others. Do some research to find an antivirus program that is right for you.
Scan Your Computer Regularly
You should scan your computer regularly for malware. This will help to ensure that any malware that is on your computer is detected and removed.
Keep Your Operating System Up-To-Date
It’s important to keep your operating system up-to-date. Cybercriminals often target vulnerabilities in outdated operating systems. By keeping your operating system up-to-date, you will make it more difficult for them to target your computer.
Use a Firewall
A firewall can help to protect your computer from malware. A firewall will block incoming connections from untrusted sources. This will make it more difficult for malware to infect your computer.
Use Caution When Opening Email Attachments
One of the most common ways that malware is spread is through email attachments. Be careful when opening email attachments, even if they appear to be from a trusted source. If you’re not sure about an attachment, don’t open it.
Be Careful When Downloading Files
When you download files from the Internet, be careful. Don’t download files from untrusted sources. If you’re not sure about a file, don’t download it.
Backup Your Files
It’s important to back up your files. If your computer is infected with malware, you may lose your files. By backing up your files, you will be able to recover them if they are lost.
How to Remove Malware and Spyware?
Step 1: Switch over the PC to Safe mode
Safe mode is a special way to predict the system-critical problem, which interrupts the normal operation of Windows. So, safe mode is an alternate boot method that makes it easier to diagnose malware infection. There are minimum programs and services in Safe Mode
So, if any malware started to load automatically into your PC, it will remove the files which are not running or active. Let’s see the steps to switch over your PC to Safe Mode .
- For this, Login to your Windows PC and click the “start” button and tap the “Power” Hold on the Shift key, and select “Reboot”.
- From the full-screen menu, select “troubleshooting” and then “Advanced Options”, then opt for “Startup Settings”. So, once getting into the Startup Settings screen, tap the “restart” button from the list of settings options.
- Next, you’ll see the window with numbered options, which is hinted as “press a number to choose from the options below”. You can select number “4” (Enable Safe mode) to enter into the Safe Mode.
After entering into the Safe Mode, you may find that your system runs faster, and then this is all because of the malware infection. Still, if the malware persists in your PC, then follow the upcoming methods.
Step 2: Delete Temporary Files
The temporary files folder can also be a carrier of malicious files. You should delete all the temporary files and folders regularly for the smooth running of the system. Removing the temporary files would also clear the unnecessary clutter from your system and free up valuable space.
Windows 10Windows 11
Remove Temporary Files from Windows 10
Here are the steps to eliminate the temporary files on Windows 10:
- Open the Run command window.
- Type %temp% and hit the enter key.

- This run command would navigate you to this path: C:\Users\[username]\AppData\Local\Temp, that is, the temp folder.
- Select all Files and Folders of this folder and delete them. Don’t hesitate to delete them, as they are not essential for any of your tasks.

- Next right-click on the Recycle Bin and select Empty Recycle Bin.

Remove Temporary Files from Windows 11
On Windows 11, it is easy to remove Temporary files. Here are the steps:
Open Windows 11 Settings from the Start Menu.
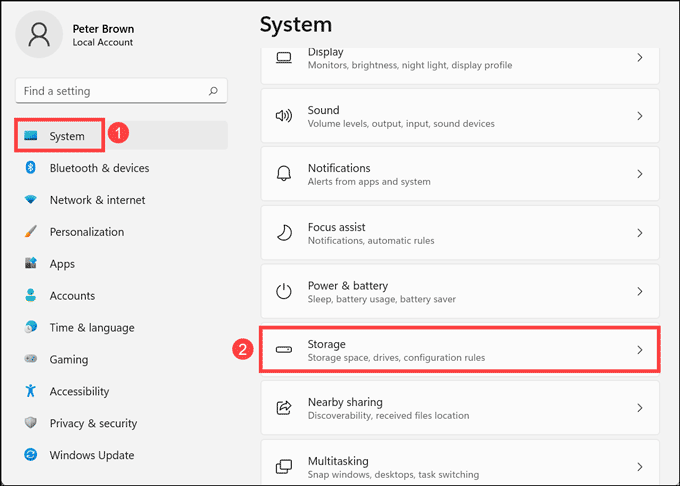
From the left pane, choose System settings and click on Storage from the right.

Click on the Temporary files option.

Tick all the boxes that you want to delete and click on Remove files.

Step 3: Uninstall Suspicious Applications
It is best to uninstall the suspicious applications, which you don’t remember installing, as they might be a potential malware program. Here are the steps to uninstall applications from Windows 10 and Windows 11.
Windows 10Windows 11
Uninstall Suspicious Apps on Windows 10
- Right-click on the taskbar and select the Task Manager.

- Watch out for the applications that are consuming the system memory even though you did not install or launch them.
Right-click on the suspicious application and open its file location.

Delete the file from its root location.
Open Control Panel and click on Uninstall a program and check for suspicious apps. One by one, select and uninstall them.

Uninstall Suspicious Apps on Windows 11
Right-click on the Start button and select Task Manager from the list.

Look out for the applications which are unnecessarily consuming the system resources without actively running.
Right-click on such applications and open their file location.

Delete all files from the targeted folder. Some files won’t be deleted as the application is still active.
Open Control Panel and click on Uninstall a program.

Check for suspicious apps. One by one, select and uninstall them.

Step 4: Remove System Restore Points
The system restore points can also have the potential to contain malware, so delete those to ensure that all the traces are removed from your PC. To be safe, you can remove all the restore points which are contracted to the malware.
- To do this, press the “Windows + pause break” keys to open the System window from the control panel and choose the “System protection”.

- From the System Properties window, select the drive whose system protection is located (Local Disk: C) and click “Configure” and “Ok”.

- Tap the “Delete” button to delete the restore points for your system. Now, the small confirmation dialog window will persist, click “continue” to remove all the restore points on the selected drive.
Step 5: Reset Web Browser Settings
Browsers are the Gateway for Malware. Malware will enter your system in many ways, but most browsers are the gateway to the web as well as the malware. There is definitely a risk involved when you download a file from unofficial websites or an attachment from an unsolicited email. Along with that, security vulnerabilities in the web browser programs themselves might sometimes lead to malware exploit.
It is best to reset the browser to its original state after a malware infection. Here are the ways to reset different web browsers.
Google ChromeMozilla FirefoxMicrosoft Edge
Reset Google Chrome Browser
Here are the steps to reset the Google Chrome browser:
Launch Google Chrome, click on three dots at the top right corner, and choose Settings from the menu.

On the Settings page, click on the Advanced at the left pane.

Under Advanced settings, click on Reset and clean up.

Next, click on the Reset Settings button to finish resetting the Chrome Browser.

How to Control a Chrome Extension’s Permissions
Reset Mozilla Firefox Browser
Follow these steps to reset the Mozilla Firefox:
Open Mozilla Firefox, click on the menu button at the top right corner, and select Help.

Under Firefox Help, choose More troubleshooting information.

On the Troubleshooting Information page, click on the Refresh Firefox button under Give Firefox a tune up. This is on the right side of the page.

On the warning pop-up, click on Refresh Firefox.

Reset Microsoft Edge Browser
On Microsoft Edge, follow these instructions to reset it:
Launch Edge browser, click on three horizontal dots at top right corner, and select Settings from the menu.

Under the settings page, click on Reset settings on the left pane.

Click on Restore settings to their default value.

Next, on the Restore settings pop-up, click on the Reset button.

Step 6: Install and Scan with an Anti-Malware
As of now, you’ve removed the unnecessary files to protect your PC from threats. Now, it’s time to update or install the anti-malware to get rid of the remaining malware.
Summing Up
Both malware and spyware can be extremely harmful to your computer. Malware can delete files, corrupt data, and even disable your computer altogether while spyware can collect sensitive information like credit card numbers and login credentials without your knowledge or consent. If you think your computer may be infected with either malware or spyware, it’s important to run a scan with an anti-malware program as soon as possible. Stay safe out there!
Is spyware a virus or malware?
Spyware is a type of malware that hides on your computer, tracks your activities, and steals sensitive information such as credit card numbers and passwords.
What are examples of spyware?
Some common examples of spyware include keyloggers, screen capture software, and browser hijacking software.
How do I know if I have spyware?
If you notice your computer running slowly, unexpected pop-ups appearing, or strange activity happening on your account (such as unauthorized purchases), you may be infected with spyware.
What is a Keylogger?
A keylogger is a type of spyware that records everything you type on your keyboard, including passwords and credit card numbers. Keyloggers can be installed through email attachments, downloads from malicious websites, or drive-by downloads.
Leave a Comment Cancel reply
Comment
Name Email
Save my name, email, and website in this browser for the next time I comment.
Δ
Also read:
- [New] 2024 Approved Stream Video Smoothly Save PC/Mac Screens to YouTube
- [New] Pioneering YouTube Fitness Ideas for a Movement-Driven Viewership
- [Updated] Addressing Mute Problems in OBS Live Recording for 2024
- 「Windowsセキュリティ」開けない問題に勝つたった4方法 - Windows 10向け
- Adjust Your Video Feedback Control in YouTube
- Come Mastering Clonezilla in Windows 7 Per Creare Una Copia Del Tuo Sistema
- Complete Repair Steps for a Damaged BIOS on Windows 11 Systems
- Comprehensive Tutorial: Deploying Microsoft's Operating System Within a Virtual Machine
- Effortless Network Drive Backup with Windows
- In 2024, How to Transfer Contacts from Tecno Spark 20C to Other Android Devices Devices? | Dr.fone
- In 2024, Two Ways to Track My Boyfriends Oppo A58 4G without Him Knowing | Dr.fone
- Multi-Database Recovery Techniques in SQL Server - Exploring Three Effective Strategies
- Resolving Windows Hardware-Induced Software Clashes: Expert Advice From YL Computing
- Unlocking WinOS Command Power over Applications, Browsing
- Windows 10 - Restaurez Gratuitement Vos Fichiers Supprimés Avec Notre Logiciel Gratuit
- Title: Understanding the Distinction: Malware Vs. Spyware Explained by MalwareFox
- Author: Matthew
- Created at : 2025-01-29 17:41:51
- Updated at : 2025-01-31 18:38:40
- Link: https://win-workspace.techidaily.com/understanding-the-distinction-malware-vs-spyware-explained-by-malwarefox/
- License: This work is licensed under CC BY-NC-SA 4.0.